Apple ID frauds frequently occur, Apple's security measures are flawless?
![]() 11/21 2024
11/21 2024
![]() 498
498

How do frequent Apple ID frauds occur?
Produced by | Business Show
Attention! If your Apple phone is bound to Alipay's password-free transaction system, there may be a risk of account fraud. Recently, multiple Apple phone users have reported on multiple platforms such as Xiaohongshu that their Apple IDs have been fraudulently used, and subsequently, the Alipay password-free accounts bound to their Apple IDs were used for various types of online consumption. According to incomplete statistics, the average economic loss per user caused by this issue amounts to several thousand yuan. Searching for "Apple fraud" on HeiMao Complaints yielded a total of 4,536 related complaints.
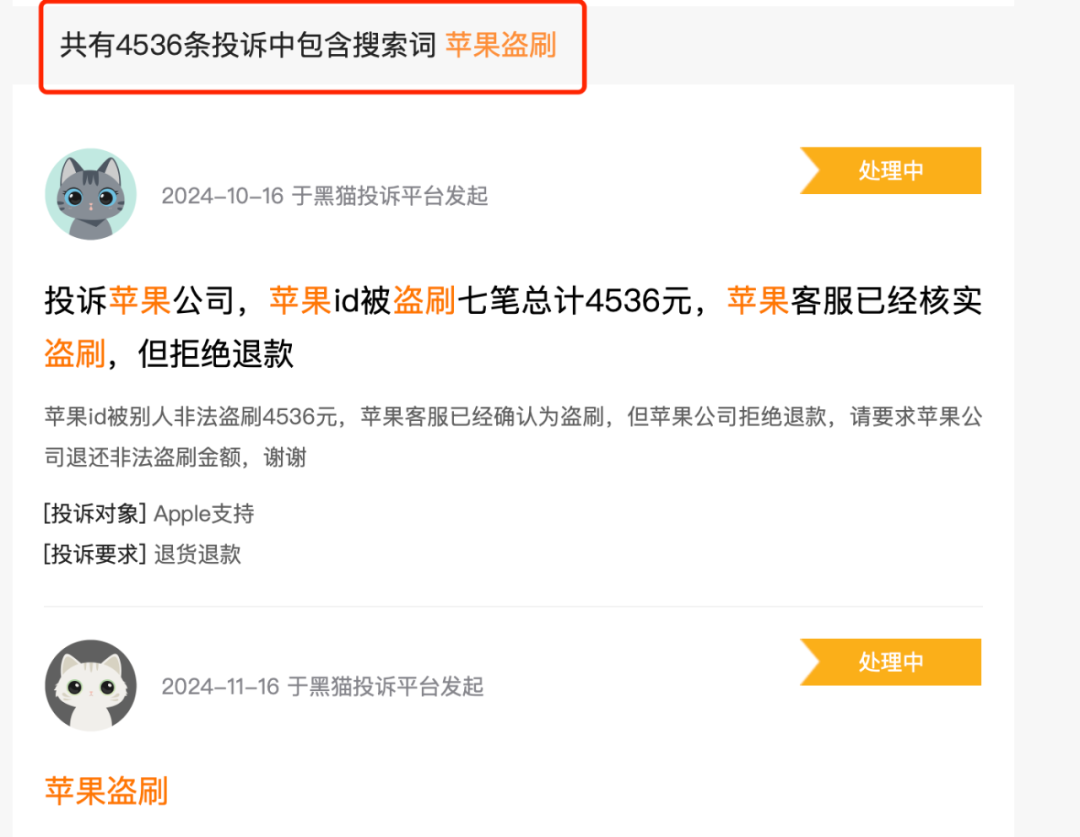
On Xiaohongshu, posts sharing experiences of fraud and fund recovery are also common.
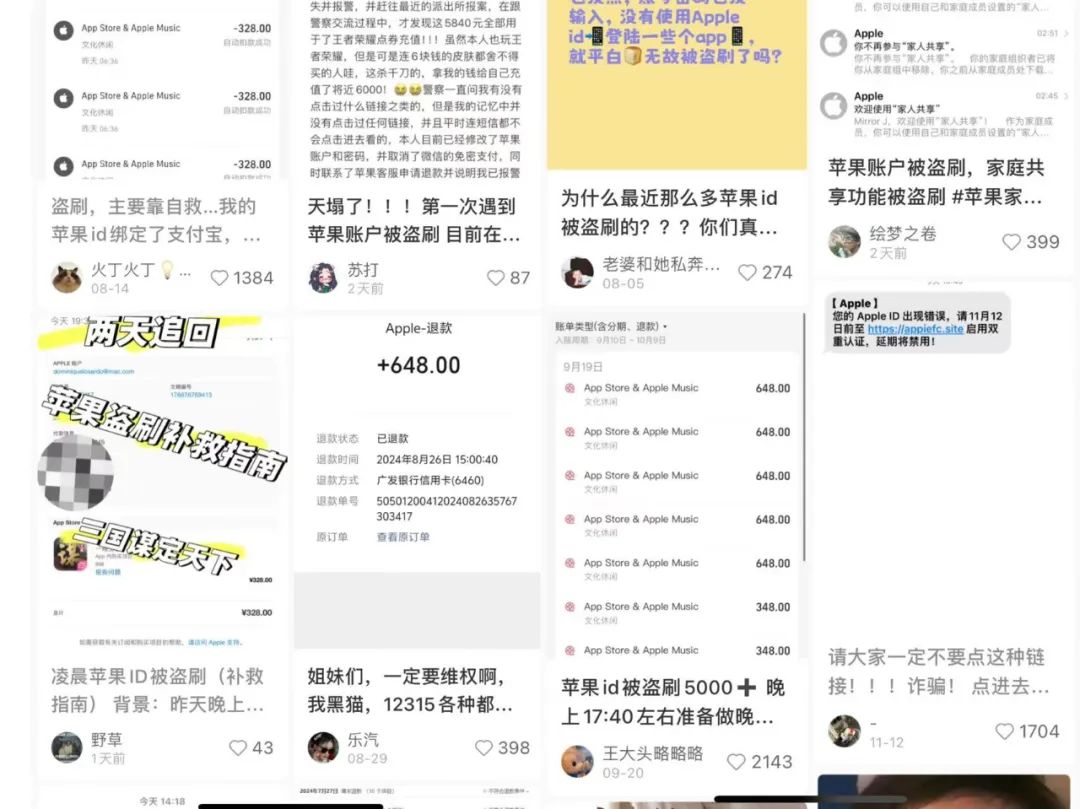
In some WeChat groups for fraud victims, some people say this is a new type of fraud they have never encountered before; others suggest it may involve technical vulnerabilities in Apple's security. How do these frequent Apple ID "fraud incidents" occur? Who should be held responsible? Besides reporting to the police and waiting for fund recovery, how should Apple users prevent such incidents?
-Business Show-01
Unknown user joins family account, fraud occurs in the early morning
On the evening of November 13, Xiao Ya (pseudonym), who works in Shenzhen, received a text message indicating that her Apple account was abnormal and needed to click on a link to enable double verification. According to Xiao Ya's recollection to Business Show, it was a highly replicated version of the Apple official website, with no differences in details, and displayed her Apple ID, requiring her to enter her password for verification. After entering her password, the verification was successful.
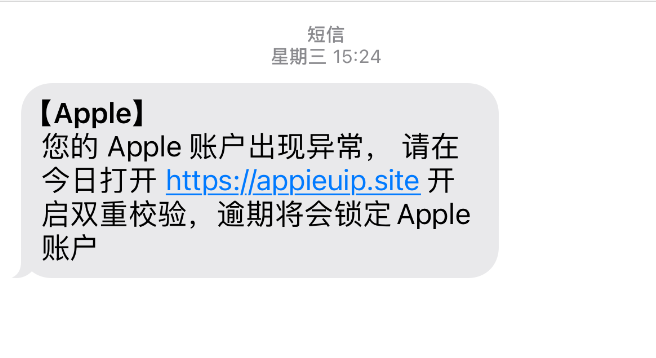
Strangely, when Xiao Ya woke up on the morning of November 17, she discovered that her account had been fraudulently used for nearly 3,000 yuan.
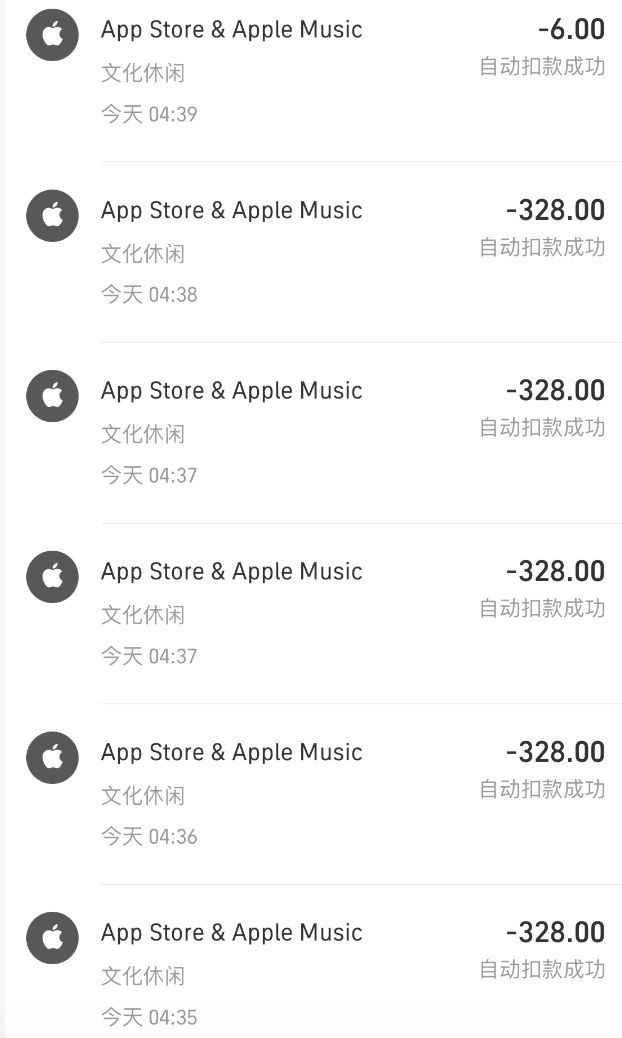
After the incident, Xiao Ya immediately reported it to the police. Through collaboration with the police, the full picture of the incident emerged: Starting at 4:28 am, an account named "Xiang Junquan" joined Xiao Ya's "Apple Family Sharing" and made a total of 13 transactions on a game called "Mir 2," totaling 2,880 yuan. At this time, due to multiple similar transactions, Xiao Ya's bank detected anomalies and locked her bank account. Subsequently, at 4:46 am, "Xiang Junquan" immediately exited Xiao Ya's family account and erased all traces of their presence.
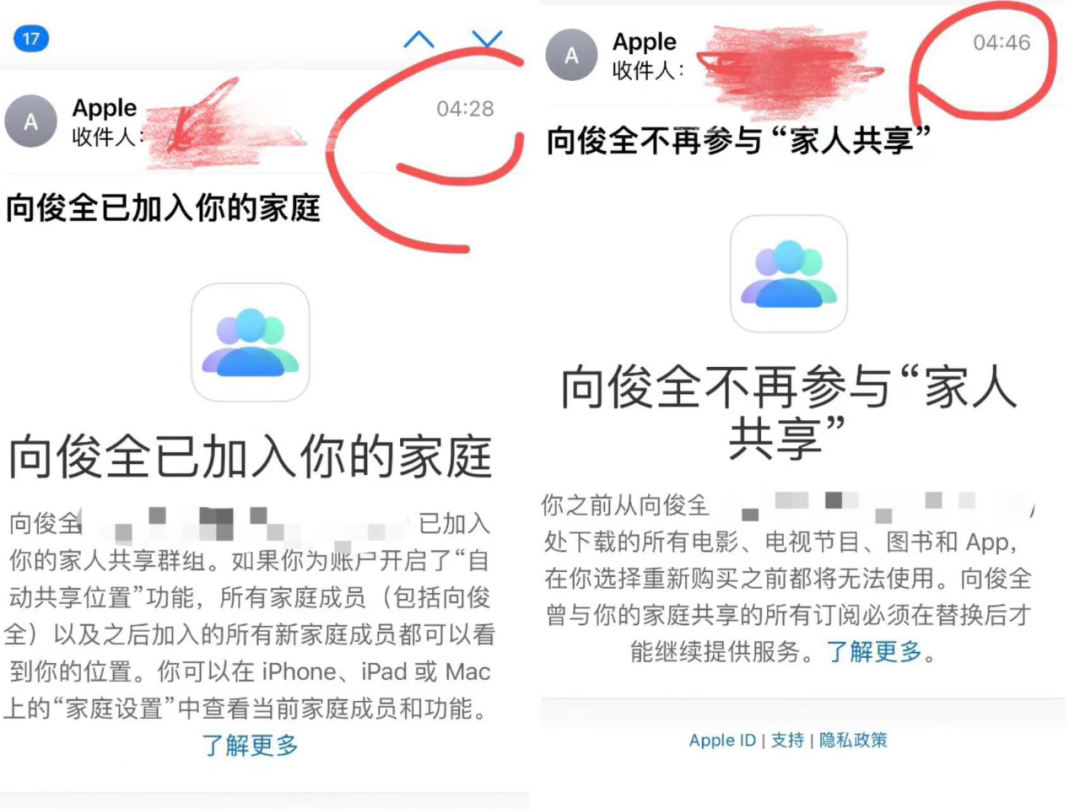
So, how did "Xiang Junquan" join Xiao Ya's family account? Xiao Ya checked her iCloud email and found that on the afternoon of November 13, she had received a notification that a foreign number had been added to the "double verification security phone category."
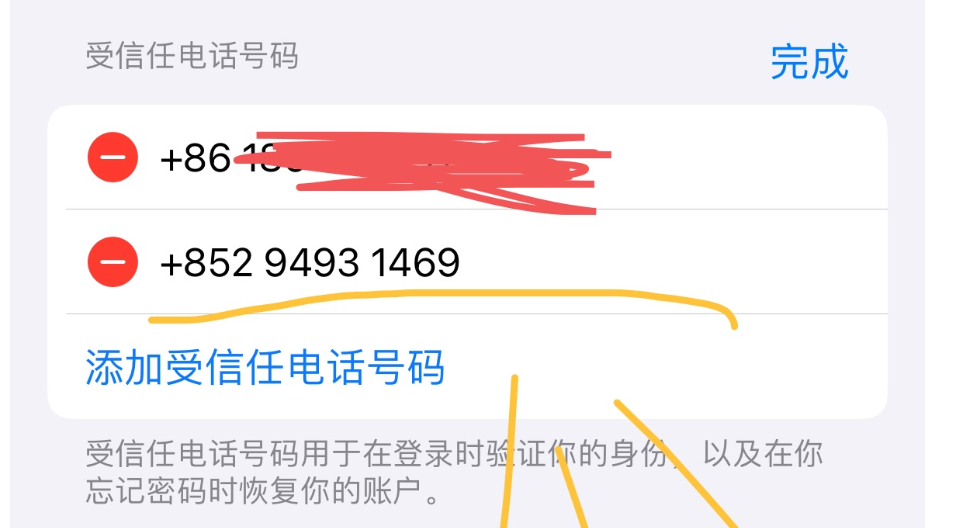
Xiao Ya told Business Show, "The iCloud email is not commonly used, and I didn't see this email before the fraud occurred." She therefore judged that it was this trusted phone number that helped "Xiang Junquan" join her account. After reporting to the police, Xiao Ya also shared her fraud experience on Xiaohongshu, attracting many comments. It turned out that there were many victims with similar experiences recently, mostly in Guangdong. Coincidentally, Biao Biao (pseudonym) from Shantou told Business Show that she also received a text message starting with 1069 on the afternoon of November 13, prompting her to verify her Apple account. After entering her Apple account and password on the website, Biao Biao also completed a secondary verification. Until 4 am on November 17, an ID named "Liu Jingbo" entered Biao Biao's family account and made a total of 17 transactions, 15 of which were 328 yuan each for in-game purchases in "Mir 2," and a couple of small transactions for Kuaishou top-ups. Due to insufficient bank balance, even Biao Biao's Huabei credit limit was deducted.
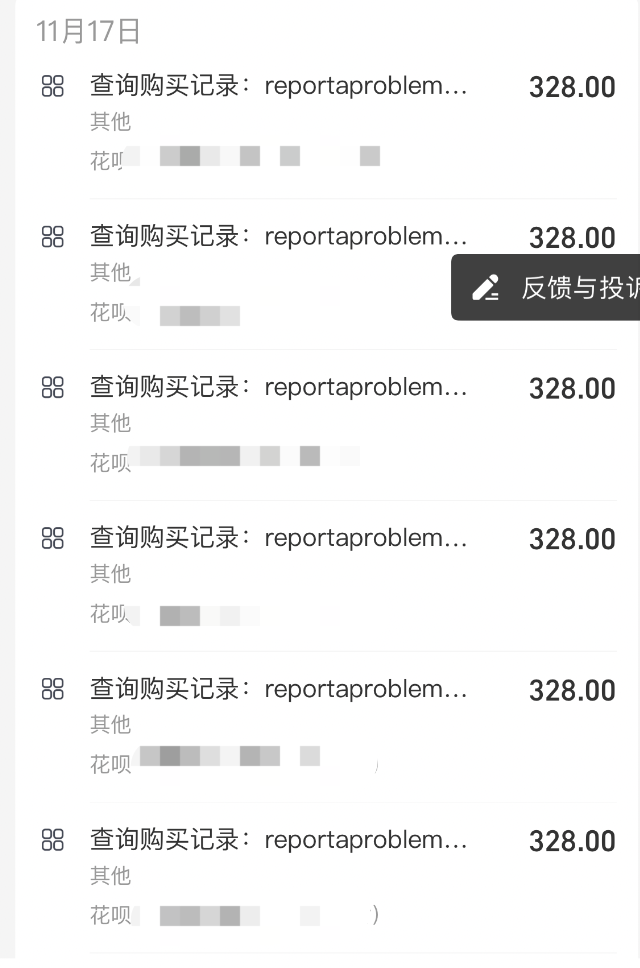
At that time, Biao Biao immediately noticed the unusual transactions, but she was powerless as she didn't know the source of the fraud. She could only unbind her accounts one by one, disable password-free payments, and remove "Liu Jingbo" from her family users. Like Xiao Ya, Biao Biao also clicked on a "phishing website," and her Apple ID was also enabled for Alipay password-free payments. The difference is that there was no other trusted phone account on Biao Biao's phone. Currently, Biao Biao is applying for a refund from Apple, but her initial application has been unsuccessful. After reviewing many posts on Xiaohongshu, Biao Biao said, "There are only two appeal opportunities, and most people are unsuccessful on both attempts. I have tried channels like HeiMao Complaints and 315, but I feel that the possibility of recovery is not high."
-Business Show-02
Difficult fund recovery, who should be held responsible?
In fact, as early as October 2018, Apple phone users from various parts of the country reported encountering fraud incidents with Apple Pay. At that time, multiple media outlets reported that over 700 people had been victims of fraud.
Searching on HeiMao Complaints, Business Show found 4,536 complaints related to Apple fraud. In August this year, multiple fraud victims also emerged on Xiaohongshu. Their experiences were mostly similar to those of Xiao Ya and Biao Biao, involving phishing websites to obtain users' accounts and passwords, and these users had also bound Alipay password-free transactions. Most incidents occurred in the early morning, when most people are asleep, and an unknown user joins the victim's family sharing and initiates fraud.
Many victims on Xiaohongshu said that the funds fraudulently used were directed to different places, some used to purchase in-game currency in games like "Honor of Kings" and "Mir 2," and others used for top-ups on apps like Kuaishou and Douyin.
In some case sharing, users also mentioned that unerased account information on lost mobile devices could also be fraudulently used and may even experience "secondary fraud." Moreover, these secondary fraud victims may still be fraudulently used again after changing their account passwords.
Through discussion, they found that the underlying processes were strikingly similar: Users' accounts were unknowingly bound to a "trusted phone number." Through this "trusted phone number," scammers could operate their accounts again.
After fraud occurs, recovering funds becomes the biggest challenge. Nowadays, many victims' first choice is to report to the police. According to Business Show's understanding, many victims who reported to the police also indicated that they knew the possibility of fund recovery was slim; some users contacted the game companies where the funds ultimately flowed, but even with their cooperation, it was difficult to recover the funds.
A user whose funds were fraudulently used for in-game purchases in "Three Kingdoms: Strategic Conquest" said that after contacting the company's customer service, they received feedback that they would cooperate if contacted by the police.
Biao Biao told Business Show, "I have never downloaded the game 'Mir 2' and cannot contact that company. After I removed the 'Liu Jingbo' account, the specific consumption information is on that account, and I can no longer check it. How can I recover the funds?"
Ultimately, many Apple users who were fraudulently used pointed the finger at Apple. Xiao Ya told Business Show, "I had no idea that if someone joins your family sharing, they have the right to use my Apple Pay account, which is bound to Alipay's password-free function, to make purchases in the App Store. During the process of someone joining my Apple family sharing, doesn't Apple need to obtain my authorization again?"
Due to others' experiences of "secondary fraud," even after changing her Apple account password, Biao Biao still unbound all bank cards on her Apple phone.
She raised the same question as Xiao Ya, "I don't understand why family sharing can be joined without consent and allows for fund operations.""Regarding the issue of family sharing, Business Show called Apple customer service. Apple customer service stated that if users have enabled the iMessages function, after obtaining the account password, others can log in to the account and send iMessages to invite others to join their family sharing. This process does not require secondary authorization."
Faced with multiple users encountering fraud issues, Apple customer service suggested that users who encounter such situations should report to the police and increase their security awareness.
Apple's family group function, intended for user convenience, has become a loophole for this fraud. Regarding this, Business Show consulted relevant security experts, who said, "This should belong to social engineering attacks, including phishing messages, fake support calls, and other scams. Simply put, this exploits vulnerabilities in some user interaction processes rather than attacks targeting Apple's system itself involving security technology.""The security expert also stated that Apple also has certain procedural errors. Apple believes that these risks will not be exploited or will be allowed after a simple security verification, but in reality, these loopholes can be amplified when exploited by the gray market.
He pointed out that Apple definitely bears some responsibility for this. At least after a fraud incident occurs, first, as a platform, it should respond quickly and stop it; second, it should fulfill its obligation to inform, and users' accounts should undergo multiple verifications to protect the account security of Apple users as much as possible.""Li Ya, a partner at Beijing Zhongwen Law Firm, told Business Show, "Users need to verify the authenticity of such websites. Similar text messages should be opened cautiously, and payment instructions should be handled with even greater caution. Apple's product design is not a matter of 'compliance or non-compliance'; it can only be said that it may have certain flaws.""For users who have already experienced fraud, Li Ya reminded, "The first thing to do is definitely to report to the police; secondly, the relevant personnel should still communicate with Apple, explain the reasons for being fraudulently used, and inform Apple, suggesting that they should bear corresponding responsibilities for customer losses. If multiple users experience similar situations and contact Apple but see no improvement, users can report to the relevant regulatory authorities." [End]
(At the request of the interviewees, the pseudonyms Xiao Ya, Biao Biao, etc., are used in the article)





